FISHY aims at delivering a coordinated cyber resilient platform that would provide the appropriate set of tools and methods towards establishing trusted supply chains of ICT systems through novel evidence-based security assurancemethodologies and metricsas well asinnovative strategies for risk estimation and vulnerabilities forecasting leveraging state-of-the-art solutions, leading to resilient complex ICT systems, comprising the complete supply chain, particularly focusing on the IoT devices at the edge and the network systems connecting them.
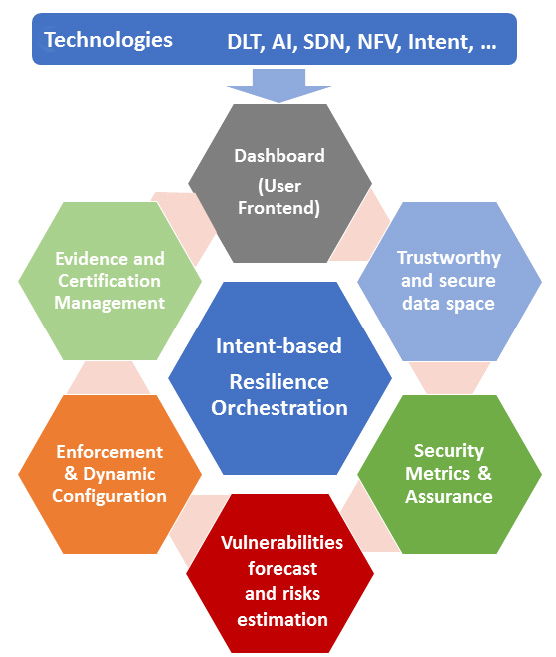
FISHY is not envisioned as an incremental integrated cybersecurity solution, but rather as an extensible and programmable framework that can flexibly orchestrate the whole set of ICT systems and security controls. The aim is to provide an innovative cyber resilience framework, where complex ICT systems performance in an entire supply chain may be analyzed in terms of security, trust and privacy impact on performance. To this end, FISHY seamlessly combines advancements in several domains, including, Software Defined Networking (SDN), Network Function Virtualization (NFV), intent-based networking, AI-based techniques, and Distributed Ledger Technologies (DLT). The final target is the creation of a trusted mosaic of ICT subsystems as illustrated in the figure.
The high-level FISHY architecture and concept is depicted in the next figure where the entire supply chain including the stakeholders is also shown. This architecture is the first version of the proposed FISHY solution and will be fine-tuned to accommodate progress evolution (requirements, design, implementation and testing) during the project life. Each stakeholder participates in the supply chain through resources and infrastructure, from data to IT infrastructure, either as provided by the stakeholder itself, or reachable through other stakeholders via core network and clouds. The main FISHY concept relies on designing a security, trustworthy and certification layer, transversal to the whole set of stakeholders in the supply chain intended to make the entire ICT supply chain system resilient, but also to correctly measure the complete security compliance and consequently trigger the required actions (mitigation, reconfiguration, etc.), making sure that guarantees for a certain level of cyber resilience are provided. It is worth mentioning that we envision FISHY to be deployed on the entire set of devices and systems in the supply chain, most notably including the IoT ecosystem. The latter is including heterogeneous IoT devices at various localities and assumes their connections to gateways or hubs, edge and cloud systems as well the network infrastructure to connect them all.
Next figure also introduces the FISHY functional architecture, where four principal functional modules are proposed: Intent-based Resilience Orchestrator and Dashboard (IRO), Security and Certification Manager (SCM), Trust Manager (TM) and the Secure infrastructure Abstraction (SIA).
The Figure also shows the key blocks within the SCM module, namely the Secure Assurance & Certification Management and the Enforcement and Dynamic Configuration, as well as the The Figure also shows the key blocks within the SCM module, namely the Secure Assurance & Certification Management and the Enforcement and Dynamic Configuration, as well as the Trust & Incident Manager and the Security & Privacy Data Space Infrastructure both into the TM module.
Starting from top to bottom, the Intent-based Resilience Orchestrator and Dashboard (IRO) module is designed SecureInfrastructureAbstraction Edge/IoTInfrastructure1 SupplyChain SecurityAssurance&CertificationManagement Enforcement&DynamicConfiguration Trust&IncidentManager Security&PrivacyDataSpaceInfrastructure Intent-basedResilienceOrchestrator&Dashboard FISHYPlatform Edge/IoTInfrastructure2CloudInfrastructure to work as the user-centric interface to translating and to orchestrating input actions into intents, to be used by other components. The Security Assurance and Certification Management is responsible for the provision of auditable, evidence-based evaluation and certification of the assurance posture of complex ICT systems, based on identified security claims and metrics, setting the roots for the definition of a pan-European process for certification of devices, processes and systems, as required in today’s in the European market. Trust & Incident manager provides the tools for assessing the security of the stakeholder’s device, component or/and system. The Enforcement & Dynamic Configuration block is responsible for making the entire system cyber resilient, even when including potentially insecure components, based on the concepts of dynamic self- configuration. Security and Privacy Data Space Infrastructure is responsible for the collection and storage of data generated from the devices, processes and components of the stakeholders’ ICT systems being part of the supply chain. Finally, Secure Infrastructure Abstraction (RIA) is the infrastructure-centric interface and works as a data interface between different Edge/IoT or Cloud infrastructures and FISHY platform.