Unveiling the Cybersecurity Tapestry: Safeguarding Supply Chains with an Innovative Resilience Approach
Supply chains are extremely delicate systems, integrated by heterogeneous components which are distributed in different domains and realms.

FISHY TIM SACM demos in Cybersecurity Congress January 2023
In this blog we summarize some of the demos performed in the FISHY demo day in the Cybersecurity Congress (January 2023).
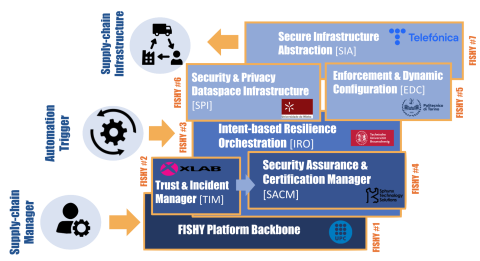
Secure Infrastructure Abstraction(SIA) & FISHY Reference Framework (FRF)
In this video blog post FISHY shares a video with a presentation about two components developed by UC3M and TID in the FISHY Project: SIA and FRF.

Key Innovations in Supply Chain Cybersecurity and Resillience that Make Sense in Today's Industry
FISHY Blog Post - Exploitation
FISHY liaisons and collaborations
In the lifetime of FISHY, the consortium has put much focus on exploring intersecting ideas through the collaboration with other European initiatives, in particular with projects

WBP TRUST use case
This is SONAE ARAUCO one of the biggest players in the world of wood-based solutions putting it simply through the use of wood, their main raw material ,and adding some resins heat and pressure.
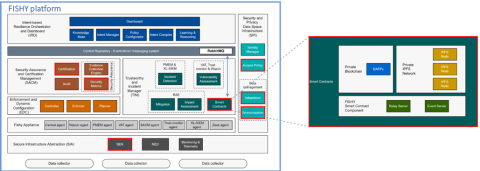
Using blockchain technology to secure security information
FISHY aims at delivering a coordinated cyber resilient platform towards establishing trusted supply chains of ICT systems. FISHY detects security threats and recommends or enforces (depending on the user’s preferences and settings) policies and mitigation actions.

FISHY SADE use case
What would happen with cybersecurity in a future world of autonomous or semi-autonomous cars?
Can hackers/thieves take control of the autonomous or semi-autonomous cars?
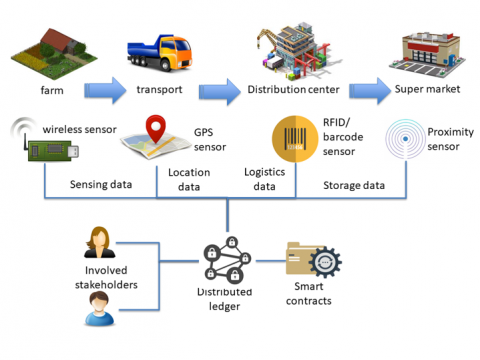
F2F use case demo
How "safe" is the food we consume?
The Farm-to-Fork (F2F) use case builds an agricultural supply chain scenario, leveraging a decentralized trusted process intended at facilitating all interested stakeholders to receive information about the conditions under which the products have been cultivated, stored and transported during their entire lifetime.
WRAPPING-UP THE HORIZON RESULTS BOOSTER EXPERIENCE WITH INNOVATION MANAGEMENT TRAINING AND A HANDS-ON WORKSHOP
The FISHY team has been leveraging the advantages of the European Commission’s initiatives since the start of the project and, in early 2023, we were accepted for a third and fina