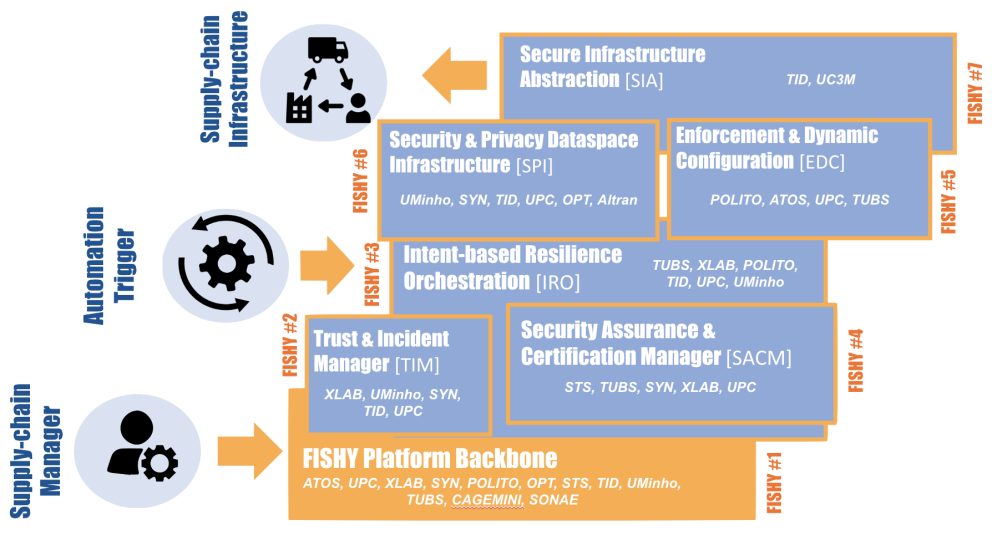
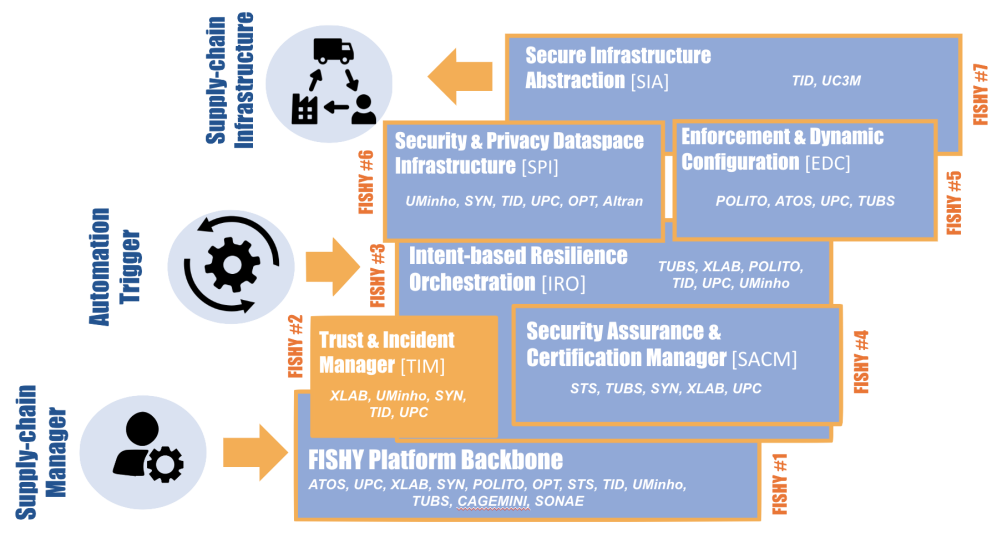
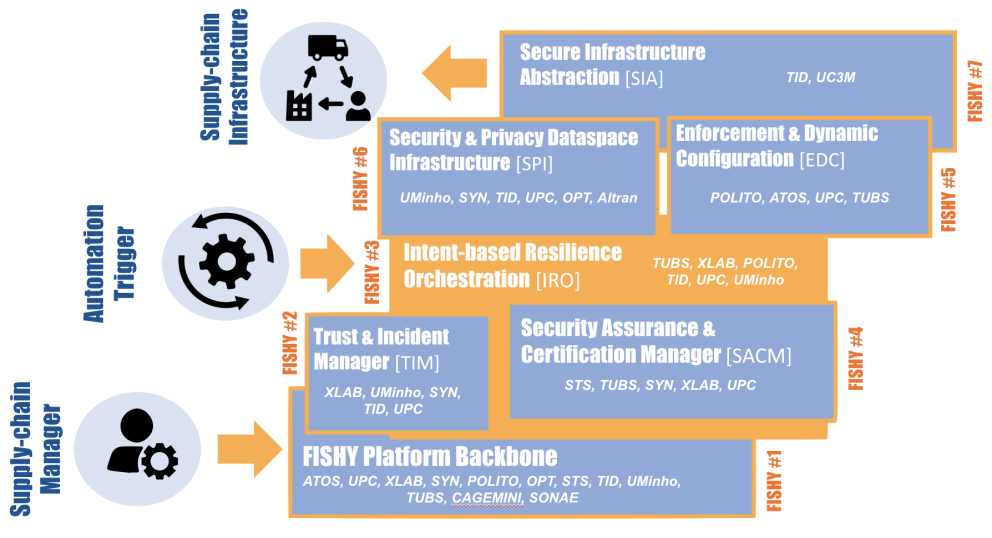
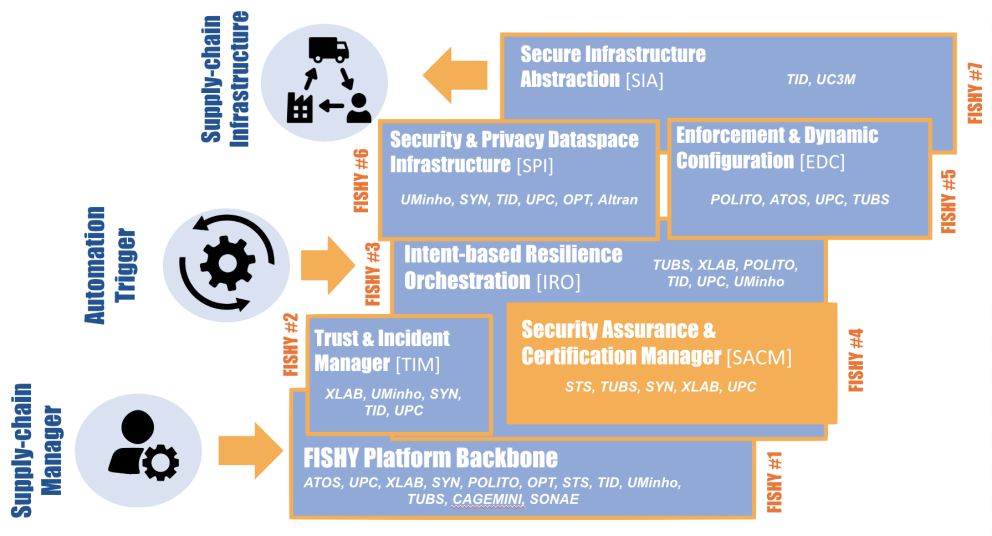
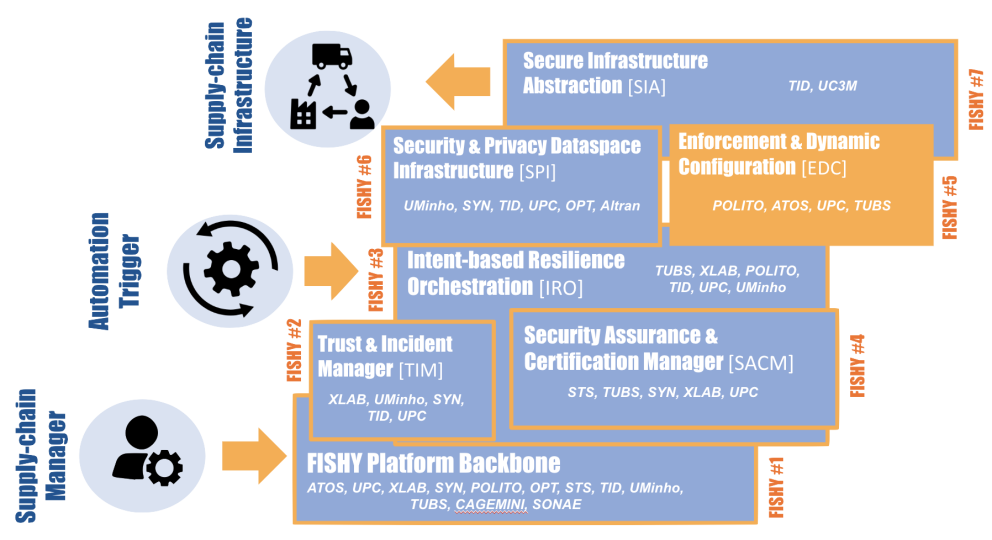
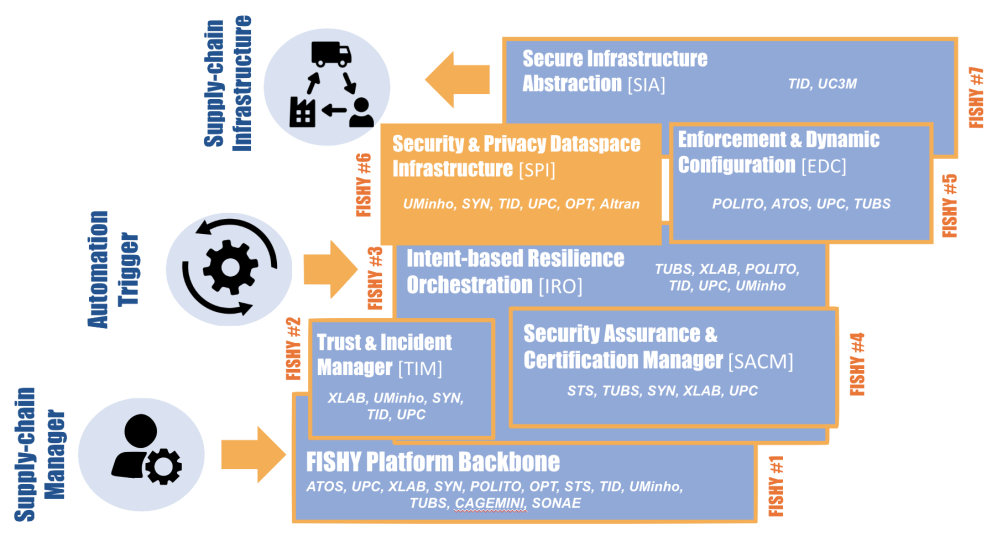
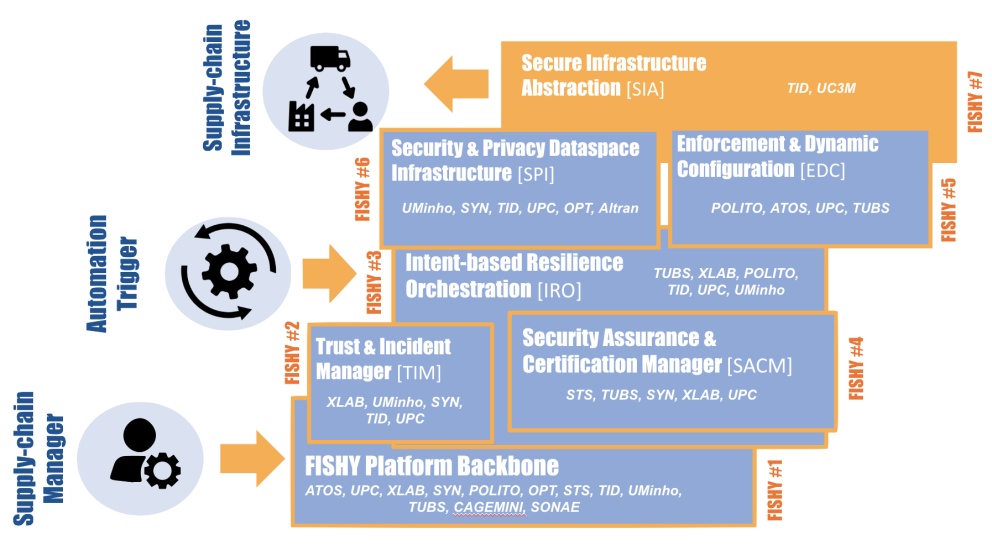
Ker 1Dashboard & Platform
Easing FISHY platform usability, making the whole system user-friendly and ready to be used for different users according to their expected profile and thus permitted functionalities.
This platform designed to support the specific needs inherent to the heterogeneous and diverse supply chain scenario also suportting the hybrid model FISHY is envisioned to support. It is not vendor-specific, with a modular approach to ensuring cybersecurity that offers monitoring, and security and resilience enforcement all-in-one tool (these functionalities are typically separate and vendor-specific).
Benefits
- Cybersec information readiness
- Automation of cybersec pipelines
- non vendor specific and able to integrate with existing solutions
Use cases
-
Smart Manufacturing
Centralize the management of users, including different user profiles, and support system’s administrators in their responsibility of monitoring the security of the IoT devices and systems they operate -
Autonomous driving
Support the administrators of the IT systems of the three type of actors of the F2F chain to monitor the security of the IoT solution they operate in a flexible and credible way, supporting also blockchain-relevant trust/security management -
Farm-to-fork
An entry point for users that will centralise certain security aspects of the supply chain of software versions of IoT devices embedded in vehicles, enabling the management of in-vehicle user identities and facial identities, and having appropriate forms for the management of data

Ker 2Vulnerability Forecast & Risk Estimation (TIM)
When addressing the resilience of supply chains in their complexity, a platform that provides vulnerability forecast, risk estimation and mitigation must consider the heterogeneous nature of supply chain infrastructures as an important driver of architect
This toolset allows users to monitoring and gathering metrics from supply chain infrastructure, performing analysis, raising alerts, proposing mitigation actions. It enables users to set up custom scans based on any user-provided script or by using the integrated vulnerability scanners to run the scanning tasks on-demand immediately or set up automatic repeated schedules, being alerted to new vulnerabilities discovered.
Benefits
- Continuous monitoring of infrastructure
- Imediate notification of anomalies
- Automated recommendations for mitigating actions
Use cases
-
Smart Manufacturing
Continuously perform vulnerability scans, classify vulnerabilities (risk-based) and send reports to the IRO. It will open incidents when an IoT device not registered to FISHY is detected and escalate the level of criticality if the incident is not dealt with -
Autonomous driving
Detect diverse types of attacks based on continuous monitoring of specific points/ security probes defined by the F2F IT systems' operators and define rules based on which incident/threats are detected -
Farm-to-fork
Assess the risk of attacks by analysing the logs that the SADE services will have available, and collect the logs from one of the enabled services, analyse them and generate a mitigation response which can be via REST API or by passing messages in a specific RabbitMQ queue

Ker 3Intent-based Resilience Orchestration (IRO)
Solution translating high level intents into configured policies, and interact with the system response using AI techniques
Automation of the interactions between the user defining high-level intents and the system applying high-level policies. The utilization of high-level language to apply policies and communicate with the network will save operation expenses for the network administrator.
Benefits
- Automation: Set, modify or delete security policies at scale using high-level intent language
- Transparency and Control: Using other modules of FISHY to monitor the IT infrastructure, IRO shows notifications and alerts about the network condition, recommand actions, and react based on the situation
- Security: Using predefined policies, IRO can react to detected threats automatically or after confirmation from the user, and enforce security rules using other FISHY components
Use cases
-
Smart Manufacturing
Allow for the registration of systems and devices to FISHY, to be communicated to the EDC and the SPI. It will send notifications, alerts and suggestions for actions and security audits to users -
Autonomous driving
The IRO is required to offer to the administrators of the F2F IT solutions: a) the capability to register their system and define the rules to be monitored; and b) to receive notifications, alerts and suggestions for actions and security audits of their systems -
Farm-to-fork
Indirect use allowing the generation of policy definitions to be applied by the EDC. The intents will be generated by other components based on the analysis and processing of the data obtained from the infrastructure of the SADE use case by these other components

Ker 4Security Assurance and Certification Manager (SACM)
An enhanced framework for system events' management, including metrics from different sources and promoting co-relation with added semantics
Organizing data related to infrastructure events and enforcing privacy and Access Control rules, including Identity Management. This solution translates high-level intents into configured policies, and interact with the system response using AI techniques.
Benefits
- Access Control (AC) policy and rules definition and enforcement technology
- Identity Management strategy, which is fundamental in a supply chain environment where different users' perspectives and demands must coexist
- Data sanitization and flow control from low-level on-premise components, according to previously defined privacy rules
Use cases
-
Smart Manufacturing
The module will be used to receive from IRO the registration of new IoT devices and keep an updated list of registered devices -
Autonomous driving
The module will be used to manage user authentication and ensure that requests are secure. It is expected to provide ways to register and authenticate for IoT device and car manufacturers -
Farm-to-fork
The SPI is required to receive the information from the F2F IT systems and pass it to the inner components of the FISHY platform ensuring anonymisation

Ker 5Security & Privacy Dataspace Infrastructure (SPI) Functionality
An enhanced framework for system events' management, including metrics from different sources and promoting co-relation with added semantics
Organizing data related to infrastructure events and enforcing privacy and Access Control rules, including Identity Management. This solution translates high-level intents into configured policies, and interact with the system response using AI techniques.
Benefits
- Access Control (AC) policy and rules definition and enforcement technology
- Identity Management strategy, which is fundamental in a supply chain environment where different users' perspectives and demands must coexist
- Data sanitization and flow control from low-level on-premise components, according to previously defined privacy rules
Use cases
-
Smart Manufacturing
The module will be used to receive from IRO the registration of new IoT devices and keep an updated list of registered devices -
Autonomous driving
- The module will be used to manage user authentication and ensure that requests are secure. It is expected to provide ways to register and authenticate for IoT device and car manufacturers -
Farm-to-fork
The SPI is required to receive the information from the F2F IT systems and pass it to the inner components of the FISHY platform ensuring anonymisation

Ker 6Enforcement & Dynamic Configuration (EDC) Functionality
Framework leveraging a capability model instead of the traditional refinement techniques based on logic rules
The EDC allows an administrator to effortlessly configure various security controls (e.g., a firewall or a VPN terminator) through high-level declarative policies that are automatically translated into a series of optimal low-level configurations. Its innovative refinement process will consider the current network landscape topology and its configurations to avoid inconsistencies and issues in the deployed rules. Its component architecture is tailored to supply chains needs focussing especially to regulatory obligations (e.g., GDPR) and violations/compliance of service level agreements.
Benefits
- A capability model empowers the core of the EDC, allowing an administrator to add support for new types of security controls with ease. Adding new security devices is performed by describing what they offer (e.g., this device is a stateful firewall, supports traffic rate- limiting) without writing ad-hoc code logic
- The use of a high-level policy language grants the administrators the ability to quickly and easily describe what the network functionalities are in a way closer to the human language, without worrying about their actual implementation, which is demanded to the EDC itself
- The EDC seamlessly supports both physical and virtualized security controls and allows the administrators to configure mixed networks containing both types of devices.
Use cases
-
Smart Manufacturing
Will apply security policies to mitigate risks, attacks or intrusions detected, applying security configurations when a non-compliance situation is detected. The request is expected to come from the IRO or the SACM -
Autonomous driving
Mainly used to apply security policies on the infrastructure to mitigate possible risks, attacks or intrusions detected. It applies security configurations when any security policy is not complied with, by request from the IRO or the SACM -
Farm-to-fork
The EDC is required to decide the baning of specific IPs and blockchain wallet IDs when these are issuing an attack; other similar policies may be defined based on the specifics of the IT solutions in place

Ker 7Secure Infrastructure Abstraction (SIA) Functionality
Point-of-access to interact with NFV infrastructure resources, with secure end-to-end communications across the ICT supply chain
Model-based support for seamless and secure inter-domain connectivity, and for the orchestration and automation of network security functions. The connectivity patterns and the North-bound interfaces are designed to support the specific needs inherent to the heterogeneous and diverse supply chain scenario also suportting the hybrid model FISHY is envisioned to support.
Benefits
- OSM-enabled network function orchestration
- Able to support virtualization environments based on VMs (OpenStack) and containers (Kubernetes)
- Secure multi-domain connectivity relaying on IPsec
Use cases
-
Smart Manufacturing
This component will ensure the collection of telemetry from the IoT Hub and of information logs from the WLAN controller to then send them to the TIM, EDC or SACM components -
Autonomous driving
The module will be used as part of the securitisation of services, facial identity management and certified version management in vehicles. Communication will be done in a secure way through the NED, which will allow restrictions or configurations to be applied if intrusions or risks are detected in the vehicle -
Farm-to-fork
In the F2F use case, the SIA is required to be able to transceiver information from cloud-based IT platforms that support IoT and blockchain technologies