The importance of Open Source Software and of the Communities associated with it highly contributes to the excellence of European research and development, and for the health and prosperity of the European industrial landscape. In line with the European Commission’s Open Source Software Strategy, FISHY contributes to the innovation and autonomy of Europe’s digital infrastructure, particularly in the security and resilience of supply chains.
To guide these contributions, we defined the five pillars of open research
- A FISHY public repository
- KER-specific upstreaming
- Community engagement
- contribution to standards and
- Open research - that promotes the collaboration between researchers, the dissemination and reuse of innovation, and the sustainability of the technology developed in this project.
To follow the progress of this community engagement, we use several metrics: GitHub contributors to KER; social media followers of lead partner; and research papers and conferences exposing the KER.
Project results have been contributed to different standardization efforts to maximize their industrial impact, and more specifically their application to the scenarios identified in the use cases. Standards activities of all nature (SDOs, industry associations, open-source communities) have been tracked, analysing the most relevant opportunities, and bringing not only results as direct contributions to existing activities, but also supporting the emergence of new activities based on relevant FISHY outcomes. The project team has sought the collaboration with other related research projects.
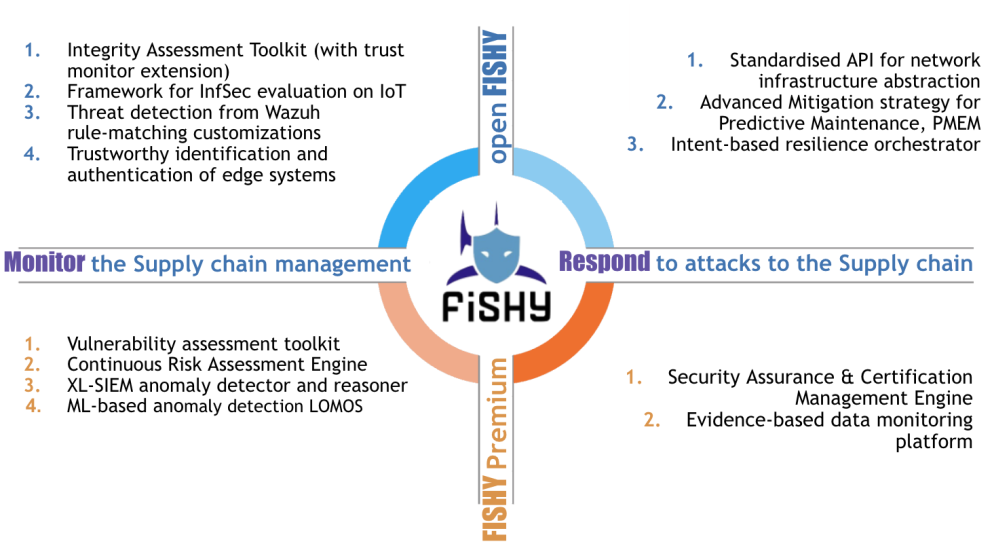
KER 1: FISHY Platform
Platform designed to support the specific needs inherent to the heterogeneous and diverse supply chain scenario also supporting the hybrid model FISHY is envisioned to support.
Current stage: There were 2 versions in IT-1, one in UPC (with F2F and WBP use cases integrated) and one in CAPGEMINI premises with SADE use case. There has never been a version in SYN. This was for IT-2. Then for IT-2 these 2 versions have been migrated to the FISHY Reference Framework. In the FRF again we have two versions, one for F2F and WBP, and another one a little tuned (with extra menus) for SADE use case.
KER 2: FISHY Trust & Incident Manager

Toolbox to monitor and gather metrics from supply chain infrastructure, performing analysis, raising alerts, and proposing mitigation actions
- TIM-Deployment
- Appliance-Agent-Deployment
- Central Repository
- Appliance-Agent-Deployment
- Trust Monitor
- Advanced Mitigation strategy - PMEM
Current stage: The TIM components are in the finishing stages of deployment and validation with the use case partners. Concretely, VAT and WAZUH were already deployed and validated. XL-SIEM, RAE, PMEM and LOMOS deployment is almost done and then these components only need to be validated. The Central Repository has also already been successfully deployed and validated. Business Model Scalability: The technology is scalable by design, based on well-established technology.
KER3: FISHY Intent-based Resilience Orchestration
The FISHY core technology translating high-level intents into configured policies, and interact with the system response using AI techniques.
Current stage: The IRO is currently containerized and deployed in UPC premises as well as in the FRF, including multi-tenancy and Keyclock authentication. An IRO Dashboard is developed and integrated with the FISHY Dashboard in the FRF. IRO is integrated with the Central Repository in order to get information about alerts through the API and through RabbitMQ for event based messaging enabling user notification. IRO is also integrated with EDC through the Central Repository to enforce policies. Moreover, IRO has integrated the EDC graphical interface to easily receive recommendations from EDC allowing the user to select best remediation decision. IRO integrated Smart Contracts verification to trustworthiness of the received events. Smart Contracts events are received using RabbitMQ consumers subscribed to the Central Repository.
KER4: FISHY Security Assurance & Certification Manager

Auditing and reasoning security metrics tailored to the pilots infrastructure, and collecting certifiable evidence from the pilots infrastructure.
Current stage: For the current state : SACM tool if fully deployed in the FRF (Kubernetes environment). Evidence Collection Engine (as part of the SACM tool) is communicating/collecting data from the pilots (use cases) directly in the FRF environment or via the Fishy Appliance (FA) framework.
KER5: FISHY Security & Privacy Dataspace Infrastructure

An enhanced framework for system events' management, including privacy enforcement and metrics from different sources, and promoting co-relation with added semantics; it comprises also an Access Control engine and a Policy Management unit to provide security services.
- SPI implementation including Data Management module to provide format conversion (to CEF format) and privacy protection function
- Zeek Log collection, which adapts Zeek architecture to the requirements of the FISHY project. The work includes Zeek scripts to accommodate external interface for log storage
- Zeek Log analysis, a set of Python functions to facilitate the exploration of network metrics and design of Zeeq scripts according to metrics definitions
Current stage: Keycloak was implemented in a Docker-based architecture, and it was already used for user authentication for most FISHY components. Moreover, it was used for application authentication, too, for the components in the SPI itself and other web services-like FISHY modules. The metrics taxonomy and security event format are in a first-draft version. The correspondent software module to implement the data organisation are fully operational. A RabbitMQ data handler, implemented in a Docker-based architecture too, was also deployed and it is ready to use. SPI also implements privacy enforcing techniques - so far, cryptographic and anonymity techniques were already tested.
KER6: FISHY Enforcement & Dynamic Configuration

Framework leveraging a formal model of security control capabilities instead of a traditional refinement techniques based on policy transformation rules.
Current stage: EDC initial PoC released, EDC based on 4 web services, each one exposing an API that allow the management of its features and workflow through a dashboard (web-based GUI accessible via browser). The EDC is currently a Docker container and leverages Python and Java to perform the policy refinement. It is currently deployed in the F2F and WBC where it automatically generates stateful firewall configuration for banning users and devices. Moreover, it is able to generate configuration rules for the proprietary security controls used in the pilots (e.g., to enforce Ethereum policies). The EDC components can be managed independently with their EDC-specific GUIs. Furthermore, the functionalities that are needed to implement the sophisticated FISHY workflows have been offloaded to the IRO and are hence available in the FISHY dashboard.
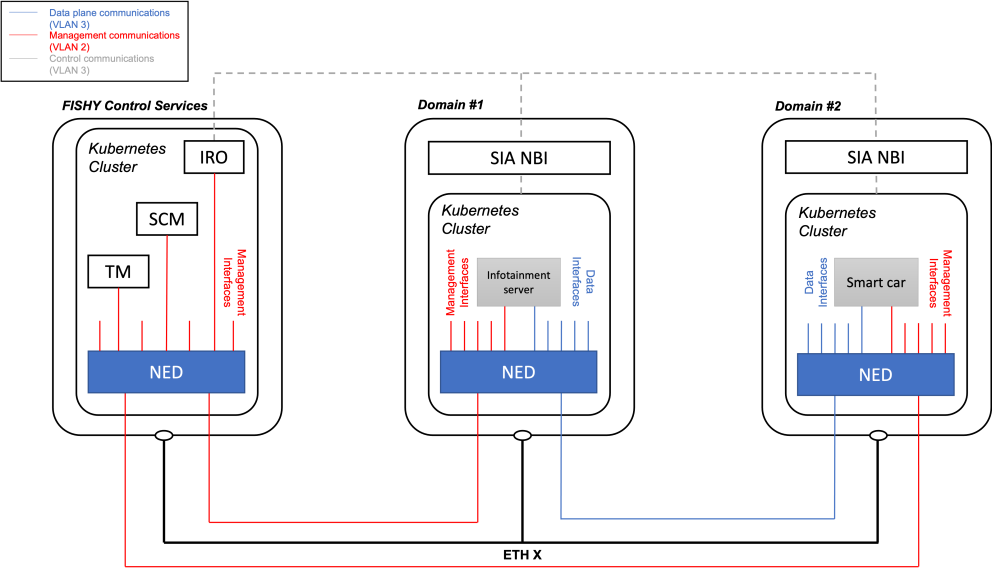
KER 7: FISHY Secure Infrastructure Abstraction
FISHY technology that supports secure end-to-end communications across the ICT supply chain providing a point-of-access to interact with NFV infrastructure resources.
- CCIPS
- OSM NBI: The original version Software-driven-Connectivity-Orchestrator, evolving towards being integrated as an OSM feature
- L2S-M or http://l2sm.io
Current stage: The SIA components (NED, Monitoring and orchestration elements) have been developed, integrated and validated in the project use cases. The current version is based on Kubernetes and Open Source MANO (OSM), and available within FISHY IT-2, constituting the core of the FISHY Reference Framework (FRF)