TRust Monitor demo in SADE use case
The Trust Monitor tool allows to manage at a higher level the remote attestation process introducing flexibility and independence from the attestation framework used.
F2F VAT
Farm to Fork VAT demo: This is a demonstration of the capabilities and usage of the VAT component of the FISHY platform in the F2F use case.
F2F Unauthorized User
Farm to Fork Unauthorized User attack: This is a demonstration of the "Unauthorized User" attack scenario, for the F2F use case, and how the FISHY platform helps mitigate it.
F2F Unauthorized device Wallet ID Warehouse
Farm to Fork Unauthorized device Wallet ID Warehouse attack: This is a demonstration of the "Unauthorized Device - Wallet ID level" attack scenario, for the F2F use case, and how the FISHY pl
Farm to Fork Attack to blockchain node
Farm to Fork Attack to blockchain node: This is a demonstration of the "Attack to a Blockchain node" attack scenario, for the F2F use case, and how the FISHY platform helps mitigate it.

FISHY White Paper #2
Key Innovations in Supply Chain Cybersecurity and Resillience that Make Sense in Today's Industry

FISHY pitch deck
We have made avaialble the pitch deck for each of the 7 Key Exploitable Results in this presentation.
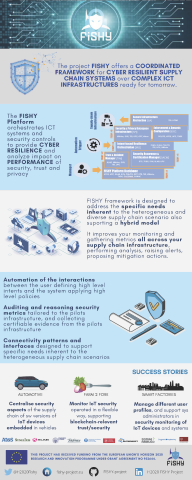
2nd FISHY roll-up
This our 2nd FISHY roll-up prepared for our General Assembly in Maia (Portugal) next week.
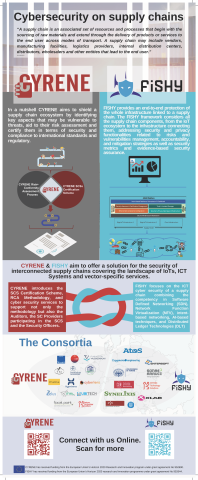
Joint CYRENE-FISHY infographic
Here you have our joint infographic with H2020 CYRENE(https://www.cyrene.eu/). Both projects aim to offer a solution for the cybersecurity of interconnected supply chains.
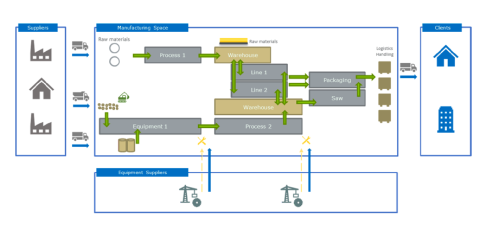
H2020 FISHY Infographic Wood-Based Panels Trusted Value-Chain
Wood-Based Panels Trusted Value-Chain use case by Sonae Arauco