How "safe" is the food we consume?
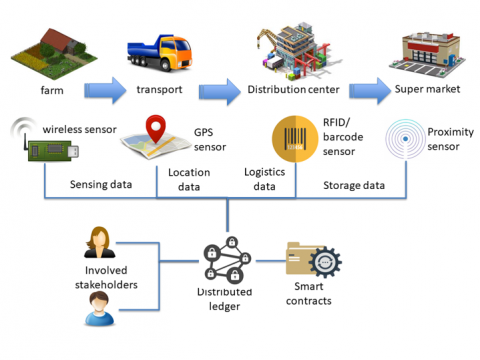
The Farm-to-Fork (F2F) use case builds an agricultural supply chain scenario, leveraging a decentralized trusted process intended at facilitating all interested stakeholders to receive information about the conditions under which the products have been cultivated, stored and transported during their entire lifetime.
The FISHY project enhances security of supply chains, enabling dymanic systems auton and on-demand security configurations.
Sensors are deployed along the journey of the food to monitor and record the critical parameters. In these critical stages of the journey IoT islands register this information in a blockchain.
The consumer can scan a RFID tag of food products and review the relevant information.
FISHY protects the Farm to Fork platform from:
Unauthorized using brute force.
Unauthorized device at wallet level.
Unauthorized device attaking the blockchain mechanism.
Unathorized decice at distributing identifier level.
In the case of a brute force attack example, the Farm to Fork platform is registered previously in the FISHY platform. When trying a brute force attack FISHY protects the Farm to Fork platform. After some trials using brute force attack the user is not allowed to access anymore.
In the case of unauthorized device at wallet level, the trasporter has previously registered the information about the food. In the case of a wallet-ID attack the federation agent has been tampered with and then the FISHY platform wallet ID is banned. FISHY protects Farm to Fork information gathering the system; and the consumer has access to immutable information about the food she consumes.
See our demo video about these attacks.