
FISHY’s Demo & Booth at the Barcelona Cybersecurity Congress 2023
In this 2023 edition of the Cybersecurity Congress, held in Barcelona during 31 January to 2 February, the FISHY project team held a booth together with other six Hor

Security and Privacy Data Space Infrastructure
Nowadays, security mechanisms are essential to every IT system to protect the users, and the information handled.
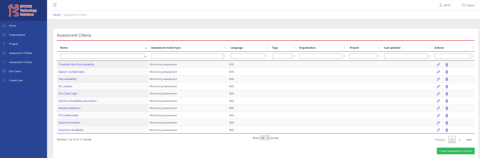
The role of Security Assurance Certification Module on a Supply Chain
The acquisition of different levels of security certification on a Supply Chain / Organization is a highly demanding process.
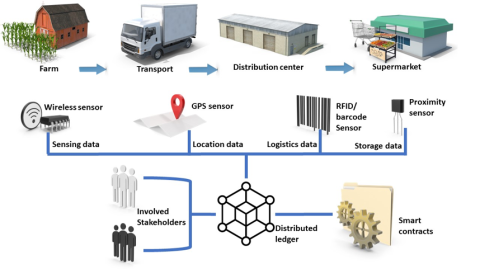
Experiences from validation of FISHY in the Farm-to-Fork use case
The Farm-to-Fork use case includes the whole food distribution chain starting from the collection at the farm, following with the transport and finally the delivery and storage at the retailer/supermarket.
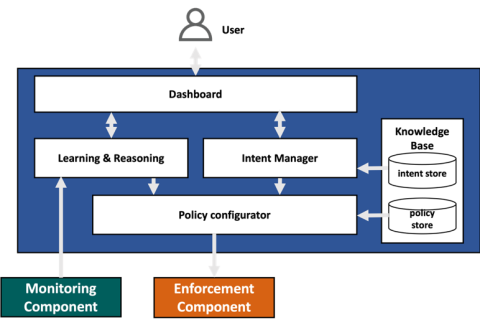
Intent-based Resilience Orchestration in Supply Chains
Network management and orchestration require high efforts and time from customers and network administrators in order to achieve the business goals. In the supply chains, networks have introduced new challenging requirements considering the heterogeneity of infrastructure, considering different owners, various and geographically distributed devices, and multiple users.
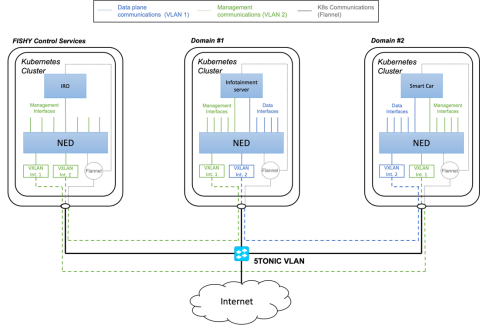
A reference framework for FISHY
In the FISHY Project, we have several components and tools that needs to be integrated and have connectivity among them.
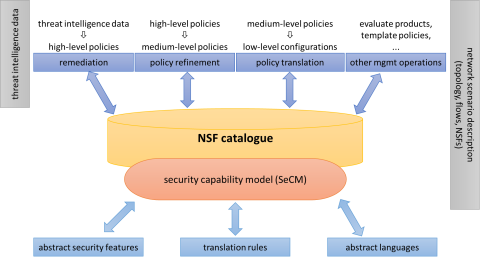
Easing the burden of network configuration: a capability-driven approach
Looking back to just ten years ago, the complexity and flexibility of software networks have taken an impressive leap forward. These advancements had a massive impact on the network administration procedures and, of course, their management costs. However, we do not witness the same level of enthusiasm when looking at the influence on security practices.

The importance of early detection of vulnerabilities and attacks for a healthy supply chain
When addressing the resilience of supply chains in their complexity, a platform that provides vulnerability forecast, risk estimation and mitigation must consider the heterogeneous nature of supply chain infrastructures .
Authors: Joao Costa, Jan Antič, Aleš Černivec, Lucija Korbar (XLAB)

FISHY, IoT Security for the automotive Supply Chain
5th Blog entry by Guillermo Jiménez Prieto (CAPGEMINI)
October 2021

The importance of security in the Industry 4.0 paradigm
4th Blog entry by Ana Machado Silva (Sonae) and José Duarte (Sonae Arauco)
October 2021