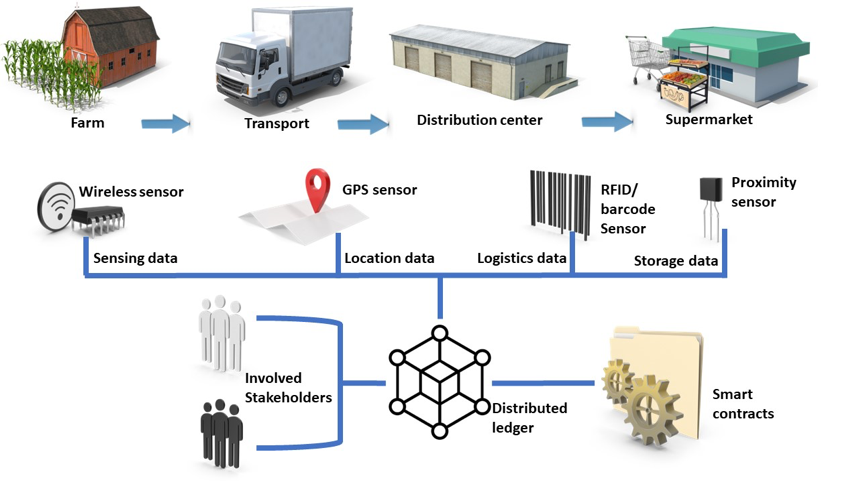
The Farm-to-Fork use case includes the whole food distribution chain starting from the collection at the farm, following with the transport and finally the delivery and storage at the retailer/supermarket. To offer to the food consumer information about the product they consume, information and communication technologies are combined to form a Farm-to-Fork IT platform. Such as platform collects data from the farm (regarding the conditions under which the vegetable are cultivated using connected sensors), from the transportation phase (regarding the conditions like temperature and humidity under which the vegetables or other food items travel), from the warehouse and distribution centers and finally from the retail points. As these platforms consist of a wide variety of hardware and software components, numerous security threats have been identified and reported in the literature ranging from brute-force and denial of service attacks to more sophisticated attacks which exploit vulnerabilities of specific devices or software components. Several market surveys and standardization groups states that “the attacks to the food supply chain systems proliferate every day”.
FISHY has considered as one of its use cases a Farm-to-Fork platform and has validated its offerings. The platform we have studied is the SOFIE Farm-to-Fork platform which is already offering a security level adopting blockchain technology, to ensure the immutability of the information inserted by the different sensors and actors. In the framework of FISHY, we have identified vulnerabilities ranging from traditional ones (like weak credentials) to more sophisticated ones (like blockchain specific vulnerabilities).
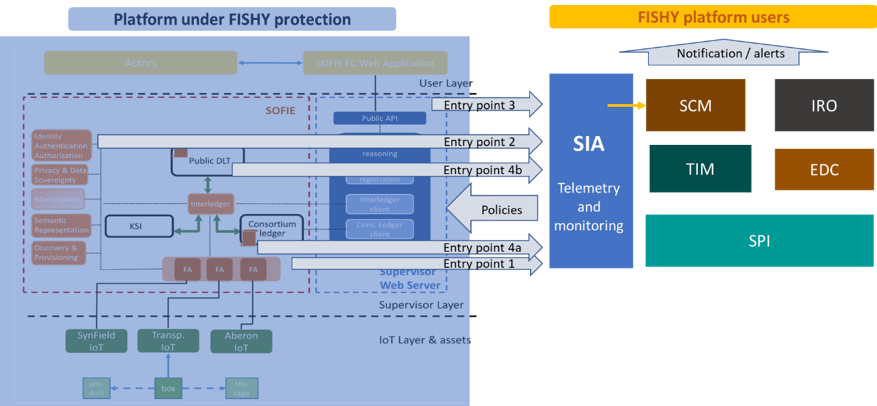
As shown in the following figure, four points of potential vulnerabilities have been identified and FISHY offers the “probes” to monitor events at these “entry points”. Exploiting the FISHY functionalities, all identified threats are detected by FISHY components, they are visualized to the FISHY users (e.g., the Farm-to-Fork platform administrator/operator) providing appropriate information supporting them to identify the point affected and finally, policies to be enforced and protect against the attacker are suggested. An additional very interesting feature offered by FISHY platform is that it detects “unusual behaviours” through its machine-learning based components, which allows for the detection of attacks that have not yet been identified in the literature and thus, no detection and mitigation methods have been defined.
For more information, visit https://fishy-project.eu/library/deliverables and check D6.2!
Antony Gonos (ENTERSOFT) and Nelly Leligou (SYNELIXIS)