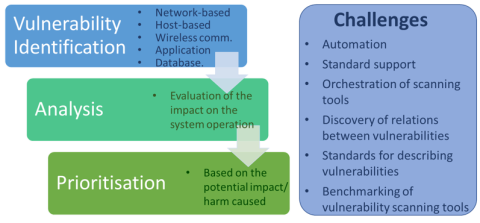
Vulnerability Assessment ment
3rd FISHY blog entry by Nelly Leligou (SYNELIXIS) June 2021
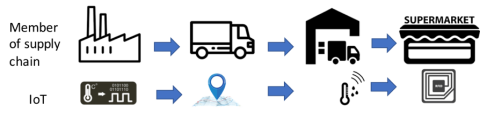
Securing IoT nodes in supply of chains
2nd FISHY blog entry by Martí Miquel (UPC) May 2021
FISHY: trustful and smart cybersecurity for supply chain
1st FISHY blog entry by José Francisco Ruiz (ATOS)
March 2021