With the increasing number of electronic, intelligent embedded systems and connectivity in the Cars plus the impending revolution of the fully connected and autonomous cars, Security is becoming a major concern in the industry, regulators and the public. A part of the adoption of cybersecurity best practices within manufacturer own teams which it is being widely adopted, main concerns about cybersecurity revolve around Software in the Automotive Supply Chain and level of the connectivity in the Connected Car.
- Software in the Automotive Supply Chain: OEMs rely in hundreds of providers for many of the embedded systems. This requires controlling hundreds of different software versions within the car, posing challenges around SW verifications and attestation and how to maintain the regularly and patch this Software and integrate them in and unified way within the automobile cybersecurity framework.
- Connected CAR: Automobile systems are now more exposed to the remote risks and tampering.
In order to tackle these two major challenges, OEMs are introducing more complex systems into the car as Firewalls and Gateways, new systems that are also prone to risks, updates and maintenance by the OEMs. Besides best practices such security testing prior to release, patching or managing a homogenous/consistent secure software development life cycle become more and more challenging. Usually industry relays in patching, dynamic security testing and penetration testing during its development phase to address some of those, but once automobile are released the increasing volume of electronic (Sensors, actuators, gateways, firewalls and ECUs) makes difficult continuous development and patching of the systems. This also leads to concerns about new functions that OEMs may consider deploying specially when sensitive user information is stored in any embedded system, this applies specially to any biometric information of the user.
Within this context, there is a trend in the Automobile industry to simplify the car electronic and embedded systems and moving most of the intelligence to the “cloud”. This trend is being boosted by upcoming technologies such as 5G, C-V2X, 802.11P and Edge computing. With this idea on mind, ALTRAN is developing a concept CAR called REMOTIS to be integrated in Spain 5G reference multi-vertical 5G Lab 5TONIC.
In the Cloud, functions like Infotainment, ADAS / AD and Artificial Intelligence (i.e. Artificial Vision, Signal Processing) functions will be provided remotely reducing the cost of the hardware embedded. Moreover, moving Capability and Functions to the Cloud/Edge allows demonstrating the capacity to easily update and upgrade those without having to update the car itself up to certain extent. Being this one of the key capacities needed for a complete secured supply chain:
- Continuous patching can be done into all the systems
- A homogeneous and consistent continuous secure software development life cycle can be applied
- Security policies can be applied to the EDGE REMOTIS
Besides this, Edge Computing offers a potentially more secure environment and framework where to develop, implement and manage potentially sensitive data from the user such as facial recognition for CAR activation. REMOTIS is deployed in the 5G 5TONIC network using ALTRAN own Edge Computing Platform called ENSCONCE, a fully commercial MEC (Multi-access Edge Computing) framework that provides the application model schema which a MEC application is required to be organized during application onboarding process. This model abstracts the various application related attributes like CPU, RAM, Disks, Network Interfaces, GPU/FPGA, traffic rules for application components etc. along with the application TCP/UDP/HTTP ports and application images (Containers). Within this context and taking advantage of REMOTIS and ENSCONCE in 5TONIC the Use Case / Demonstrator is aim to:
- Implement FISHY paradigm combined with EDGE capabilities provided by ENSCONCE
- This will allow to Offload the Security Applications into the EDGE Network
- For that purpose and as representative of the current trends in Automotive Industry, REMOTIS concept car will be expanded with the below services:
- Facial Key: The car will be activated with the user cars, being able to track and record when each user was driving it as well as information about its driving
- Sensors Secure Environment: Today, REMOTIS relies in the many of the sensors own security policies to control crypto resources such as passwords, certificates, capabilities (codecs), etc. It will be created a single entity to manage north bound those sensors capabilities
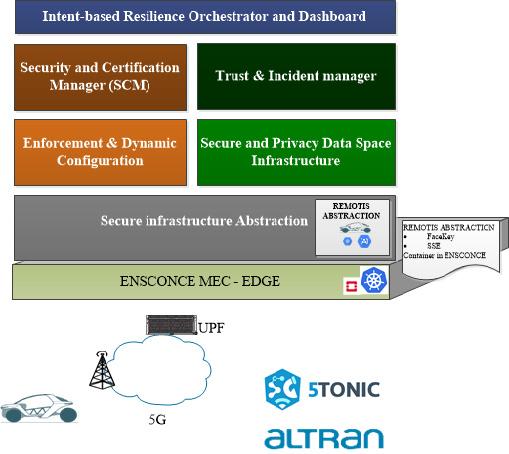
Considering the Fishy Framework, ALTRAN’s ENSCONCE will offer the compute and orchestration capabilities that will be used by upper layers to implement the FISHY framework in the REMOTIS car. For that the Secure infrastructure Abstraction functional block will provide the means to define an Abstraction or Network Edge Device of the REMOTIS car where all the crypto resources are stored, consumed and executed as well as sensitive user data such as biometrics is stored and validated. This abstraction to reside in ALTRAN’s ENSCONCE will make use of the upper layers:
- From Intent-based Resilience Orchestrator (IRO) intents to apply to the REMOTIS NEDs will be generated via the Enforcement and Dynamic Configuration, besides ENSCONCE monitoring (K8s) will feed it and upper NBI integration.
- Security Assurance & Certification Management will provide the means to certificate the different REMOTIS sensors and actuators to be integrated.
- Secure and Privacy Data Space Infrastructure will provide the means for the proper collection and storage of data generated from the devices, processes and components of the REMOTIS: Data sensors and anonymized biometric parameters.